What does the State do with our personal data? A harsh report warns about the latest leaks The Vía Libre Foundation presented a document on the regulatory framework in Argentina, more details about the Grandoreiro trojan, and less revenue in the ransomware world. JUAN BRODERSEN APR 26
Brodersen Dark News is a weekly cybersecurity news summary. The topics are selected and produced by Juan Brodersen according to these editing criteria.
⚡ TL;DR After a hot week of data leaks, it’s time to pause and reflect. Now in calmer waters, there’s room for reflection: to ask, beyond what happened, under what conditions it happened. One of the tools available to answer these questions comes from law and regulatory frameworks. This Wednesday, almost as a response to the precarious current state of the care of personal data of Argentines, a dossier was presented that aims to question, but also calls to improve, the public policy that protects privacy and the integrity of digital rights in Argentina.
From a presentation of four specialists, the Vía Libre Foundation presented a state of affairs, in addition to contributing from different legal angles not only what responsibility lies with state institutions, but how to correct outdated regulations and how to strengthen the State in its responsibility to protect the rights of citizens.
The topic takes up a good part of this issue, which had little coverage in mainstream media but which, from Dark News, we believe is fundamental to contribute towards a better handling of state responsibility in the care of personal data. I spoke with Margarita Trovato, Tomás Pomar, Pablo Palazzi, and Beatriz Busaniche to better understand the issue through their testimonies.
At the regional level, more technical details about Grandoreiro, one of the most active banking trojans in Latin America, were known after its dismantling. And the source code of Chivo, the wallet-ATM used by El Salvador, was leaked.
Globally, there were also several interesting insights about ransomware. On one hand, reports spoke of lower profits in the business. Others highlighted the enormous amount of money some groups (Akira) collected. And there was information about new groups and rebrandings.
Also, news about regulations and privacy grabbed headlines around the world due to the decision of the President of the United States, Joe Biden, to sign a project that could ban TikTok.
Lastly, something important regarding WhatsApp is that it began to accept the use of passkeys on iOS, a login mode that many experts consider more secure than traditional passwords.
And a gem for the world of digital archaeologists: Microsoft open-sourced the source code of MS-DOS 4.0 on GitHub, making it much easier to find for future research.
This email will take you 14 minutes to read.
Kingston XS1000 external SSD is a file backup solution that features speeds of up to 1.050MB/sec and high capacities of up to 2TB, providing great speed and space to store the most valuable data. It comes with a USB Type-C to Type-A cable for unmatched convenience and impressive storage capacity.

🏦 A dossier on the management of data by the Argentine State is presented
In less than two weeks, Argentina experienced a series of large-scale personal data leaks. At the beginning of April, a cybercriminal published more than 115,000 stolen photos from Renaper. Two weeks later, nearly 6 million images of driver’s licenses from Argentina were stolen and disseminated. And last Thursday, another attacker published a database with 65 million records, also from Renaper (see analysis).
For these types of cases -among other reasons-, the Vía Libre Foundation, which protects the digital rights of citizens, presented a report in dossier format in which they demand more responsibility from the State.
Beatriz Busaniche, president of the Foundation and specialist in privacy and right to information, explained to Dark News that “the project is part of the Data on the Run work program that has been developed with the support of Avina, the Indela initiative”:
It is a dossier about data in the possession of the State and we believe it is crucial to advance on this, because we have already worked on something about inferred data in the hands of the private sector, but we cannot complete this topic without analyzing in depth the management of data in the State. The dossier we published has a historical overview of the identification policies by the State, how the DNI policies were developed, the role of identification, the history of Renaper, the current panorama, and why limits must be set, including the reform of the current legislation.
The presentation had three speakers dedicated to understanding the nature of personal data, each with different perspectives. The first to speak was Margarita Trovato, a lawyer in charge of public policies at the Vía Libre Foundation, who reviewed the history of data collection in the country.
What information does the State have access to? How did the advancement of technology change the volume of data and what potential new problems were generated in the era of big data? Explained the specialist:
Naturally, the State collects personal data; originally for a registry purpose and later, over the years, with various functions, for example to produce public policies. Throughout that time, the technology of data collection, processing, and storage evolved by leaps and bounds, even over the type of data that is collected (think of biometrics) but the regulatory framework is the same: our law of protection of personal data, number 25.326, is from the year 2000.
Of course, a law that is already 24 years old “became outdated and anachronistic,” but it preserves certain minimum guarantees. “We know that the State has clear limits on what it can do with our personal data: in no case can it violate the constitutional rights to privacy, intimacy, informational self-determination, security, transparency, to mention a few, which in turn are a condition for the exercise of other rights,” she added.
In this sense, consent is an unavoidable starting point: there are certain data that the citizen must decide, actively, to provide to the State, she remembered, and they cannot be used for a purpose different from what was intended at the time they were requested.
But the most interesting is that the State has the duty of security and confidentiality: during the last years, state institutions in Argentina were “breached” (leaked, hacked), as it is said in the cybersecurity environment: from the National Directorate of Migration, which suffered a ransomware that made public exits from the country, to the Senate of the Nation, exposing internal documentation of legislators, or the Legislature of Buenos Aires.
The problem is that, according to Trovato, there are “gaps that in practice become windows to deviate from these principles” of data protection. She explains:
- The first major problem is the regime of exceptions to the consent of the owner. The State should not collect nor store more data than strictly necessary for the public policy it carries out, but the law leaves room for it to do so.
- This is even more worrying if we combine it with another of the flaws of the law: it creates a control authority with little autonomy, weak institutionally, and that is currently concentrated in the Agency for Access to Public Information (AAIP) which, as its name indicates, has a nature and technical specificity totally different.
- Finally, although in the same line, the law does not clearly describe what the security measures should be nor how the public authorities should act in the face of a security incident (for example a leak), a matter that more advanced legislations in other regions already resolve [Chile, for example, that in January approved a Cybersecurity Macro Law].
The second presentation was by Tomás Pomar, member of the Argentine Computer Law Observatory (O.D.I.A.), an entity that has a history of warning about violations of citizens’ rights (such as facial recognition in Buenos Aires). The lawyer highlighted the current challenges of the transfer of data between intra-state agencies. He told Dark News:
The absence of an adequate regulatory framework, combined with the lack of effective judicial controls and the impossibility of developing broad political consensuses on the matter, end up forming an explosive cocktail. Due to these leaks, when analyzing the constant erosion of the State’s computer systems and the warning lights that light up due to the increasing leaks, we believe in the need to communicate from O.D.I.A. its urgency and we often argue that we are heading towards an informatic Cromañón.
The reference is an analogy with the Cromañón Tragedy, which left 194 dead on December 30, 2004, in the City of Buenos Aires.
“We designate as ‘informatic Cromañón’ a potential cyber incident with tangible physical damage to the citizenry. From that definition, what happened with Renaper would not fall into this category, but, to give an example, what would fall would be if we receive an attack on critical infrastructures like the water systems or even air traffic control towers,” he explained.
“That is, a ‘tragedy’ in the most classic sense but originated in a cyberattack and, as so many other times, in the negligence and negligence of the authorities with responsibility in the matter,” closed the lawyer specialized in data protection.
To conclude, Pablo Palazzi, professor of Law at the University of San Andrés and partner in the technological law area of Allende & Brea, spoke about what laws could force the State to be more transparent about leaks.
First, he recognized the difficulty of the area: “When you talk about cybersecurity, you talk about defending yourself. You are always defending yourself and that is more difficult than going on the attack. Anyone can be hacked: security is a process, not a product,” he sentenced in a section of the presentation.
Currently, in the face of such leaks, the State should notify it before the AAIP. But at the end of 2022, Congress approved an agreement called 108+ which, although it requires the ratification of other countries to come into force, also urges agencies to make these incidents public. Palazzi closed, in dialogue with Dark News:
The 108+ agreement still has to come into force, but it has an article on security incident notifications that, as it is directly applicable, would make it mandatory in Argentina to notify incidents. That is, it would not be necessary to wait for a bill that is currently in Congress to notify incidents: Argentina would have data breach notification.
The presentation was online and can be seen in full at this link.
The full report can be read here.
🐴 More details on the dismantling of the operational base of Grandoreiro
Trend Micro published a report with more details on the dismantling of the operational base of Grandoreiro, one of the most active trojans in Latin America. At the end of January this year, the Brazilian Police carried out a joint operation with Trend Micro and ESET, which found a design flaw in this well-known malware.
This Wednesday, it was revealed that Argentina was one of the countries with the most detections during the January-April 2023 period, in addition to refreshing the way this trojan operates:
Grandoreiro spreads through phishing emails, malicious attachments, or links to fake websites. These emails often pretend to be legitimate organizations, such as banks or financial institutions, to deceive users and make them download and execute the malware. Once installed on the victim’s system, Grandoreiro functions as a typical banking trojan, aiming to steal confidential financial information. Over time, Grandoreiro has undergone various updates and modifications, improving its evasion techniques and obfuscation methods to evade detection by antivirus software and security measures.
Among the specific contributions of the company’s analysis, they highlighted:
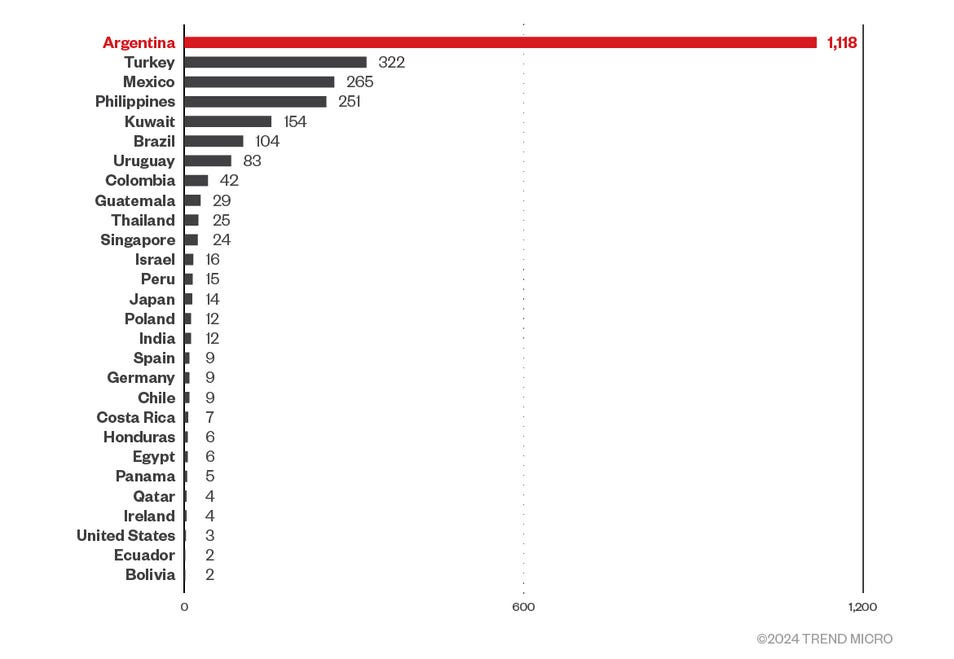
Threat intelligence data from January to April 2023 showed that Argentina registered the highest number of detections related to Grandoreiro, with 1,118 detections, followed by Turkey, with 322 detections, and Mexico, with 265 detections.
During the investigation, it was discovered that Grandoreiro used domain generation algorithms (DGA) for its C&C [Command and Control] communications. For more information, Trend generated all possible domains from the list of strings and subdomains found in multiple samples. As a result, more than 4,000 DGAs were generated, providing valuable information to pivot to the C&C servers used by Grandoreiro at that time.
The management panel is crucial for the research on the scale of attack by the threat actors and the identification of the victims. Using the open-source tool URLScan (urlscan.io), Trend recommended inspecting three active management panels with their respective locations.
The Brazilian Federal Police also managed to arrest five members who managed the malware and raided 13 homes in the states of São Paulo, Santa Catarina, Pará, Goiás, and Mato Grosso.
It is estimated that since 2019 they managed to collect 3.9 million dollars from banking customers in Brazil, Argentina, Mexico, and Spain.
Lastly, it is important to highlight that the fact that the law went against the developers of Grandoreiro does not mean that the malware will stop circulating. In fact, Dark News consulted a specialist on the subject who confirmed that detections of emails with this payload were registered.
Toward the end of the new report, you can see the indicators of compromise (IOC) and infected sites.
Bloka provides Security Operations Center-as-a-Service (SOCaaS) and Managed Security Services (MSS). It is made up of a group of cybersecurity experts and stands out for its “continuous, intelligent, and adaptive security for companies in Argentina, Uruguay, Spain, and other regions”.

📉 Less revenue in the RaaS model
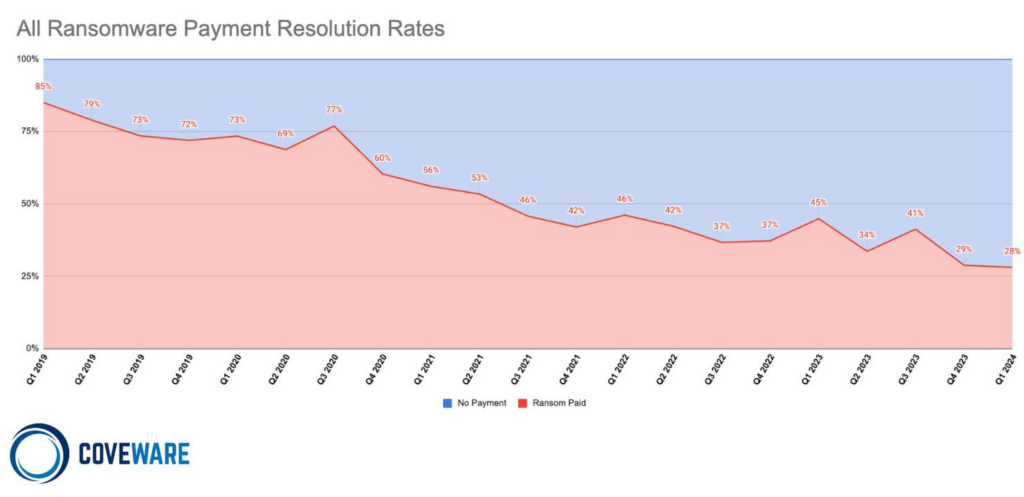
According to a study (Coveware), the extortions carried out by groups were not as profitable during the first quarter of 2024: ransom payments are at a historical low of 28%. Compared to Q4 of 2023, which was 29%, the trend is downward during the last time.
However, two factors must be taken into account. The first is the partiality of the statistics and numbers regarding cybercrime. Each company has its telemetry and, although there is a consensus in the global scene that ransomware is no longer as profitable as before, these numbers tell part of the story.
The second factor is that, despite the drop in the payment rate, the amount paid to ransomware actors is at the highest historical values, reaching 1.100 million dollars last year, according to a report by Chainalysis.
As for the first quarter of 2024, Coveware reports a 32% inter-quarterly decrease in the average ransom payment, which now stands at $381,980, and a 25% inter-quarterly increase in the average payment, which stands at $250,000.
Dark News consulted Valentina Costa Gazcón, threat analyst and CEO of V•ONE Labs, on the threat landscape of ransomware:
While there are great dismantlements, which are really impressive and often the result of coordination between the security forces of various countries, what often happens is the fall of an organization implies the fall of a “family” of ransomware that, sometimes, also rebirths, either because not all its members were caught or because the builder of the malware leaked. In addition, new groups using ransomware in their campaigns emerge every day, using developing countries to test their effectiveness, and we must also keep in mind that many decrypted families are still in circulation. Therefore, we must never let our guard down, and it is important to have the No More Ransom project page at hand to check if the ransomware decryption tool that affects us is available.
The scene, however, remains very active. Just to name a few cases, this week new groups were discovered: Embargo, Qiulong, and another self-named APT73.
Akira Ransomware, meanwhile, consolidated itself as the group that raised the most: 42 million dollars, now targeting Linux servers.
🔑 WhatsApp now accepts passkeys on iOS globally
WhatsApp announced this week that it will accept passkeys to log in on iOS, thus dispensing with single-use access codes by SMS. The news was known half a year after the system was accepted on Android. As of this Wednesday, it started to be implemented, and should be available to all users as the weeks go by.
With passkeys, the authentication of users is synchronized across all their devices through the cloud using pairs of cryptographic keys. This allows the user to log in to websites and apps with the same biometrics (fingerprint or facial recognition), or PIN they use to unlock their devices.
But Passkey logins make it harder for attackers to remotely access accounts, as they would also need physical access to a phone. Passkeys also eliminate the need to rely on insecure combinations of usernames and passwords, which may be subject to phishing or brute force attacks.
WhatsApp users can enable key verification by entering their app settings, navigating to the “Account” options, and clicking on the new “Passkeys” button.
Telecom offers Firewall services for Companies and SMEs, aimed at solving the main security needs within a network.
🔗 More info The United States applies visa bans for spyware developers
Two founders accused of the crypto mixer Samourai
General Motors collected millions of driver data and shared it with insurers
Find a vulnerability in CrushFTP, a corporate file transfer program
MITRE suffered a cyberattack by a state-sponsored actor earlier this year
Android works on a system to quarantine malicious apps
The German police shut down a DDoS service
More techniques to hide malware on GitHub